Hi all,
We are trying to configure Azure AD SAML authentication for FME Server 2022.2 . We have used the express installation and then configured an IIS reverse proxy.
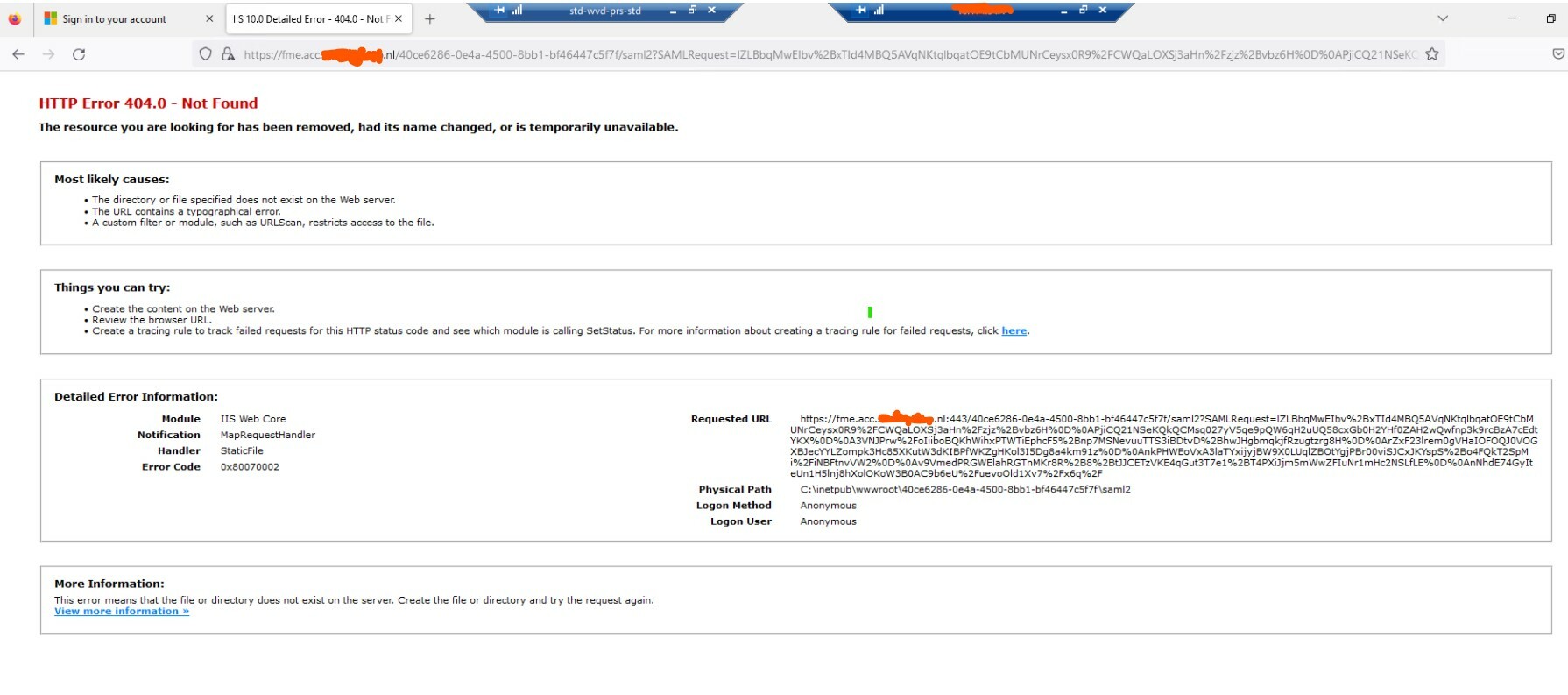
We are getting the error in the attached image. Is Azure AD SAML authentication with an IIS reverse proxy supported?