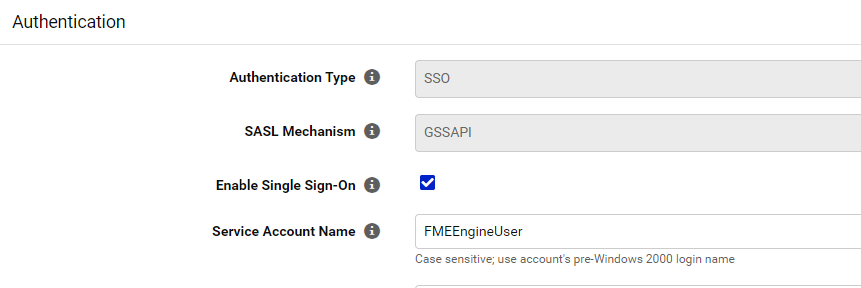
Hi!
After FME Flow upgrade from 2022.2.1. to 2023.1 our organization is not able to use login with Windows credentials (Active Directory) anymore. It seems to be similar issue to Known Issue: FME Server SSO failed login due to insufficient credentials (safe.com), the error message is Failed login by user YIIJygYGKwYBBQUCoIIJvjCCCbqgMDAu... due to insufficient credentials. We haven't changed the configuration and until now the upgrades to a newer version haven't broken login with Active Directory user.