Hello,
I currently have some workbenches which access APIs and hence have secrets within them, which is fine when this is secured on FME Flow.
I also want to set up version control, and have all of my workbenches uploaded to remote repo, GitHub.
TLDR: How can I secure my API secrets on GitHub?
So far I’ve looked into:
- encrypting my workbenches
- https://support.safe.com/hc/en-us/articles/25407644298637-Password-Protection-for-FME-Workspaces
- this seems OK, but doesnt truly secure the api secrets, it does add a level of security but it could be better
- Storing my API keys as published parameters on FME Flow
- this may be hard to manage, especially when trying to run/debug/design any API workflows
- if a user/developer accidentally hits ‘save parameters’, then this method will likely be redundant
- can become messy and difficult to manage in general
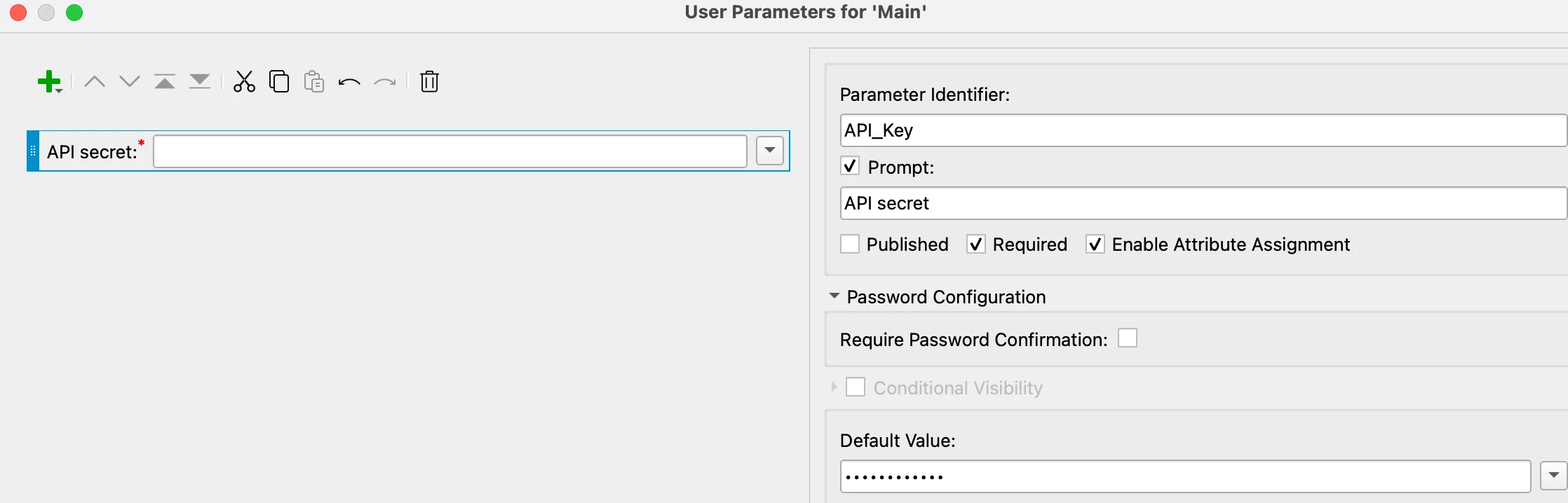
Would setting up the secret as a password parameter within the workbench encrypt it in the .fmw?
Will a password protected workbench still work on FME Flow?
What other options do I have?
Thanks.