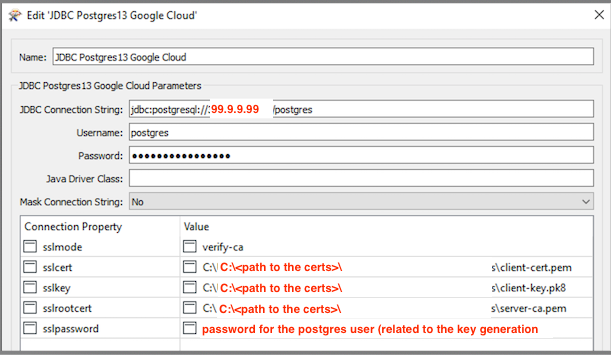
With FME Desktop 2019 and newer, Postgres and Postgis support SSL, this mode has different options as shown below in the screenshot.
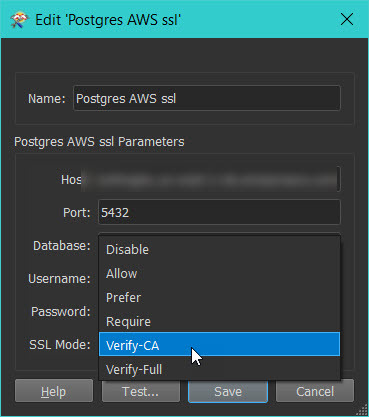
By default: Value is set to Disable
For Verify-CA and Verify-Full, options the root certificate needs to be stored when connecting to RDS instances.