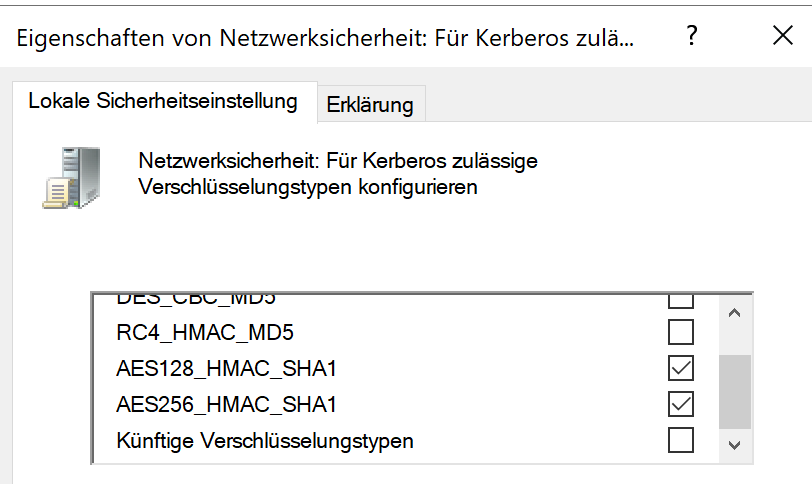
I upgraded my Development machine Thursday, and install ran smooth, import of backup ran smooth. Checked settings and all appear to match up with Staging and Production, but unable to get Single-Sign-On to function again.
Negotiation reported an error: "Failure unspecified at GSS-API level (Mechanism level: Encryption type RC4 with HMAC is not supported/enabled)".
All three of my systems use the same Service-Account, and Staging and Prod have not issue, and Dev worked fine until the upgrade.